Printing Out Secret in Azure Databricks
Hello!
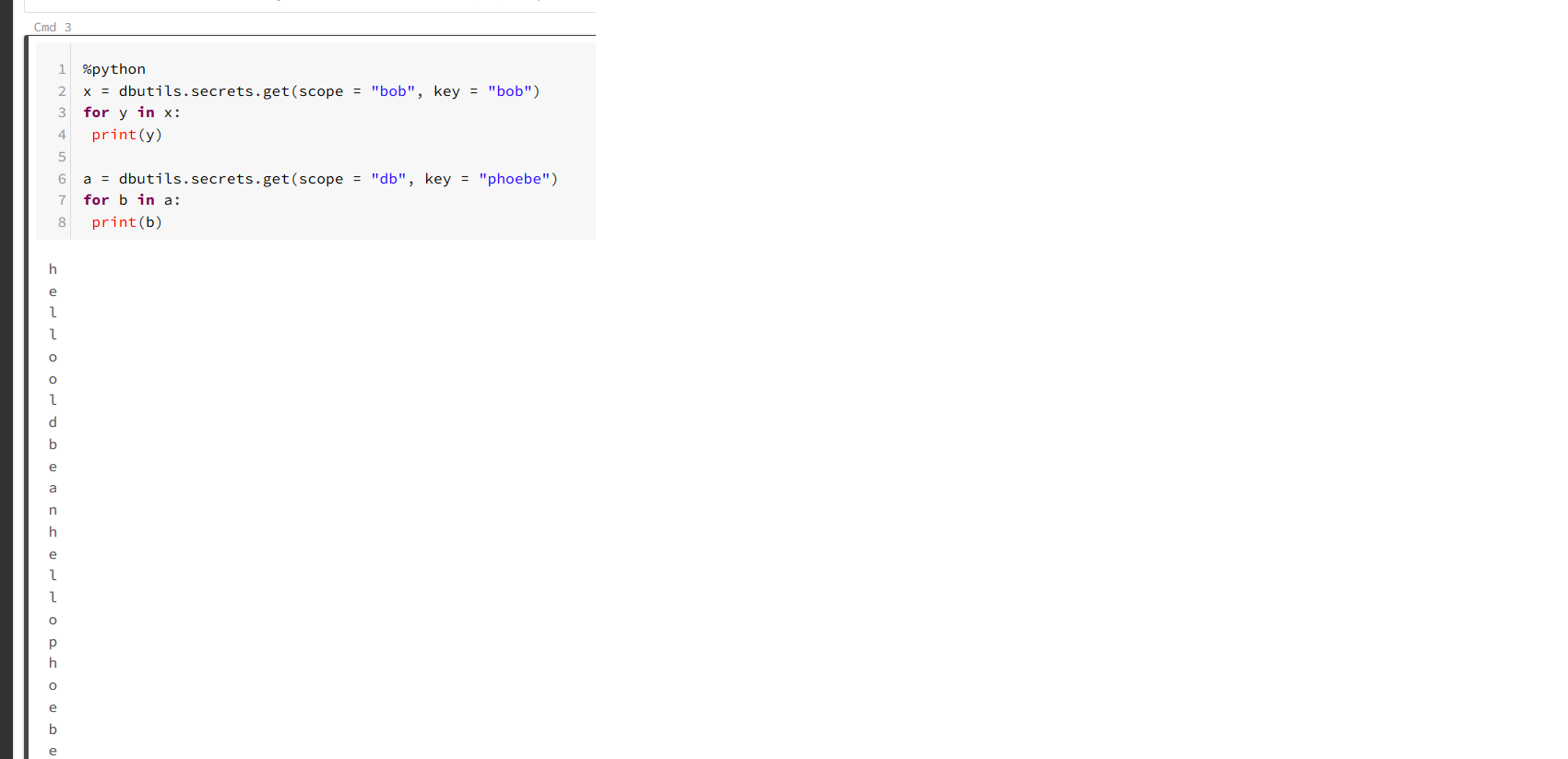
back in August I posted a “how to expose secrets in your VSTS pipelines” post that promised to do exactly that. Now funnily enough I have been playing around with Azure Databricks lately and looking into using both Azure Keyvault and Databricks-backed Secrets and Scoping and remembering my post from last month, I wondered if it was possible. Come to find out it is! I added secret to called bob to a scope stored in KeyVault and another called phoebe to a DataBricks-backed scope and I was able to print them out easily enough.
x = dbutils.secrets.get(scope = "bob", key = "bob")
for y in x:
print(y)
a = dbutils.secrets.get(scope = "db", key = "phoebe")
for b in a:
print(b)
Now as a point, secrets are supposed to be redacted when I print them out, like so -
%python
x = dbutils.secrets.get(scope = "bob", key = "bob")
for y in x:
print(y)
a = dbutils.secrets.get(scope = "db", key = "phoebe")
for b in a:
print(b)
print (x)
print (a)
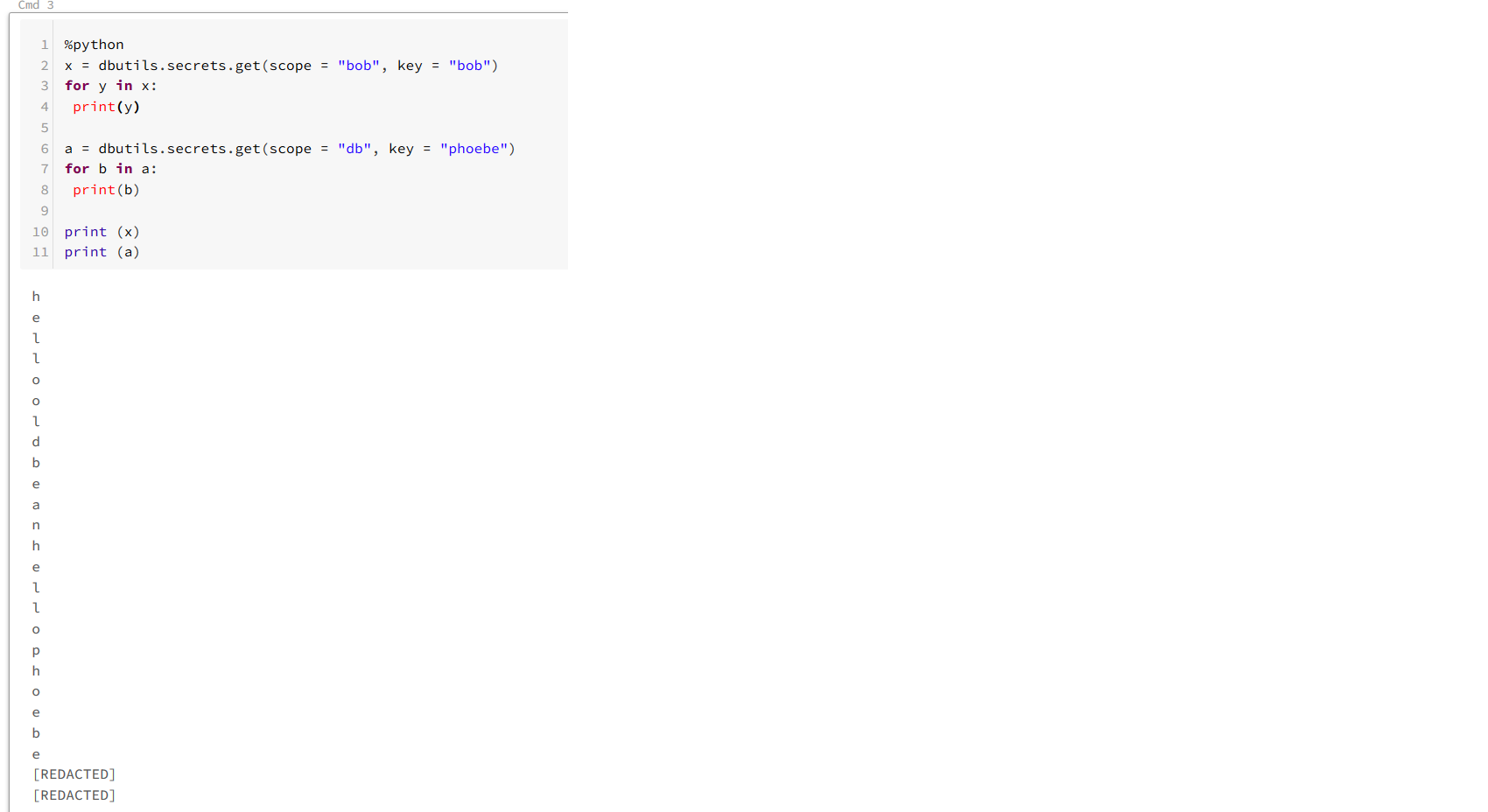
So all this is very bad, yes? Well yes it is, but just like with printing out secrets from VSTS*, there is a solution. It is possible to use Workspace Access Control to limit what it is that a user can do. By default, all users can modify workspace items. WAC locks down what it is users can do and manages permissions at a far more granular level. This may be appropriate on prod or perhaps shared workspaces.
*The fact that I can printout secrets like this has led me to wonder if perhaps it is possible to run this trick even if VSTS is using Keyvault for storing secrets. An idea for another time perhaps!
